This article covers the prerequisites for using Synthetic Monitoring for synthetic testing. For additional information, visit the following articles:
- Prerequisites for ControlUp for Physical Endpoints & Apps
- Communication Ports for VDI & DaaS (US Region)
- Communication Ports for VDI & DaaS (EU Region)
Endpoints
Depending on your region, the following endpoints must be available via TCP port 443 (HTTPS)
US Region
- app.scoutbees.io
- api.scoutbees.io
- ws.scoutbees.io
EU Region
- app.eu.scoutbees.io
- api.eu.scoutbees.io
- ws.eu.scoutbees.io
IP Addresses used for Alerts
Alert notifications are sent from the following IP addresses:
- US Region: 54.227.226.171
- EU Region: 18.156.103.107
Custom Hive connections
| Origin | Destination | Protocol | Purpose |
|---|---|---|---|
| Custom Hive | wss://ws.scoutbees.io or wss://ws.eu.scoutbees.io (EU region) | WS over HTTPS | Create a secured WebSocket connection between the custom hive and Synthetic Monitoring cloud-based backend |
| Custom Hive | https://api.scoutbees.io or https://api.eu.scoutbees.io (EU region) | HTTPS | Send test results to the Synthetic Monitoring metrics database |
| Custom Hive | StoreFront/NetScaler | HTTP/S | Get published resources and open a session |
| Custom Hive | VDAs | WebSocket (default port: 8008) | Open a WebSocket (encapsulated HDX) session to a relevant VDA. Relevant only for internal StoreFront type Scouts. |
| Custom Hive | XenDesktop Brokers | HTTP/S | Get session and machine metrics and metadata about the tested published resource. Relevant only for internal Citrix Storefront type Scouts |
| Custom Hive | Omnissa Horizon (formerly VMware Horizon) Connection Server | HTTPS | Connect to Horizon HTML client |
| Custom Hive | VMware Unified Access Gateway | HTTPS | Connect to Horizon HTML client |
Custom Hive prerequisite for Citrix Storefront Scouts
You will need to allow WebSocket based sessions on the relevant delivery groups in the Citrix Virtual Desktops (formerly XenDesktop) policy to allow the headless runner to connect to the published resources. To do so, perform the following:
- Go to the Group Policy Management Console or Citrix Studio to configure HDX policies.
- Select the WebSockets connections policy setting, and allow WebSockets connections.
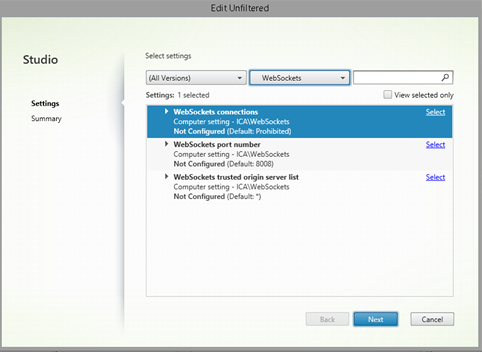
- Assign to the relevant Delivery Group and Enable the policy.
Cloud Hive Locations
| Cloud Hive Location | Hive Name (API) | IP Addresses |
|---|---|---|
| EU (Frankfurt) | eu-central-1 | 3.68.42.249 18.192.246.141 18.196.71.73 18.193.253.189 |
| EU (Poland) | polandcentral | 20.215.247.157 20.215.246.233 20.215.250.96 |
| US East (North Virginia) | us-east-1 | 44.195.57.11 3.211.41.46 18.210.30.146 54.172.165.102 |
| Asia (Sydney) | ap-southeast-2 | 54.79.113.123 3.106.81.135 13.55.189.163 54.253.81.89 |
| Nordics (Oslo) | norwayeast | 51.107.209.81 51.107.209.179 51.107.209.219 |
| Asia East (Hong Kong) | eastasia | 20.239.181.137 20.239.88.186 20.239.92.50 |
| US West (Seattle) | westus2 | 20.80.190.2 20.80.190.50 20.80.191.31 |
| South India (Chennai) | southindia | 20.235.18.189 20.235.20.227 20.235.21.126 |
| UK (London) | eu-west-2 | 3.11.161.196 3.11.54.111 3.8.248.71 |
| Africa (Cape Town) | af-south-1 | 13.245.225.69 13.245.215.5 13.244.81.204 |
| South Central US (Texas) | southcentralus | 20.165.26.222 20.165.27.71 20.225.142.48 |
| Canada (Montreal) | ca-central-1 | 52.60.246.48 99.79.25.255 52.60.233.242 |
| Brazil (Sao Paulo) | sa-east-1 | 18.228.84.68 18.230.52.221 18.230.53.130 |