One of the most important ControlUp components is the ControlUp Monitor. It is the entity in charge of constantly monitoring all endpoints, hypervisors, and more, 24\7. The following article explains how monitors work and what permissions you must grant them to properly function.
From version 9.0, you can install the monitor with Microsoft PowerShell cmdlets. For versions lower than 9.0, you install it with the ControlUp Real-Time DX Console.
The monitor also monitors endpoints for alerts based on the triggers that you have set up, and uploads the data into our Hybrid Cloud VDI App reporting system.
The best practice is to install the monitor on its own dedicated server and provision it with the necessary resource, as explained in ControlUp Sizing Guidelines.
If you use our on-premises solution, see ControlUp Monitor Permissions & Security - On-Premises ONLY.
The Monitor in Cloud Environments
After you deploy the monitor, it will be recognized on the machine by its process, cuMonitor.
The monitor uses the following entities on its end:
- The cuMonitor.exe runs as the NETWORK SERVICE account on the monitor machine only.
- For versions lower than 9.0, the monitor uses an AD account that you configure when you set up the monitor for several purposes:
- Deploy the ControlUp Agents on remote machines (if the user had administrative rights on the remote machines).
- Connect to the machines using port 40705 in order to monitor them (for VDI App, alerting, etc.).
- The monitor uploads data to our cloud servers to populate data into the VDI App.
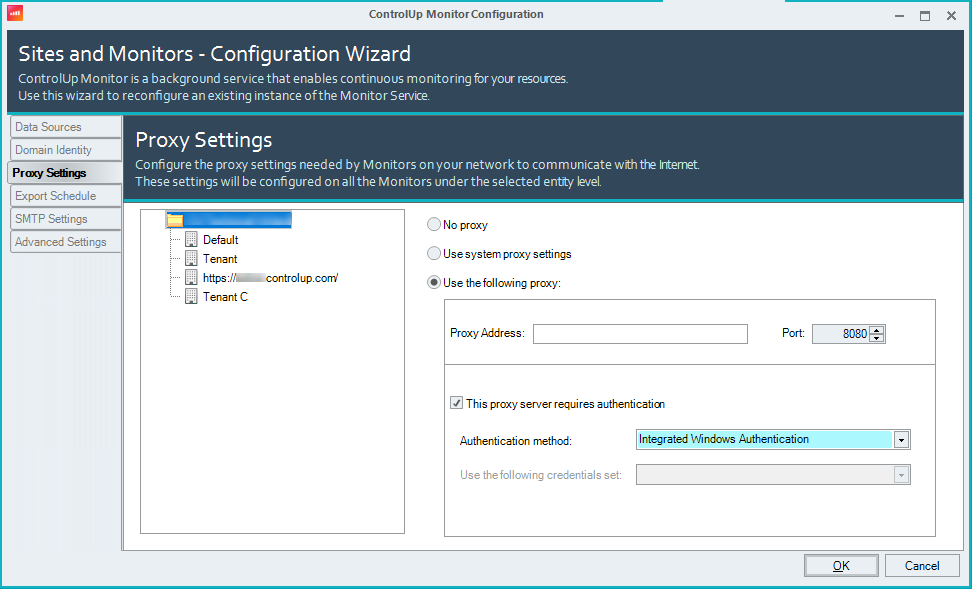
If you use a proxy, you need to configure it under Monitors Settings > Proxy Settings.
US (+Non-EU) customers:
fe2.controlup.com
fe4.controlup.com
rt-app.controlup.com
rt-app.controlup.com
cu-ca-us.controlup.com
mp.controlup.com
insights-hec.controlup.com
EU customers:
fe1.controlup.com
fe3.controlup.com
rt-app.controlup.com
rt-app.controlup.com
cu-ca-eu.controlup.com
mp.controlup.com
insights-hec.controlup.com
Permissions in the Security Policy pane (from 9.1)
From version 9.1, you can you can assign specific credentials to specific users. For more details, see here.
If you use the optional Independent Sites mode, you can define permissions per site. Users will only have access to log into sites that you grant them permission to. For more details, see here.
Permissions in the Security Policy pane (pre 9.0)
For versions lower than 9.0, you must delegate the proper security permissions for the AD account that the monitor uses. In the ControlUp Real-Time Console > Security Policy pane, you must grant the following permissions:
- Perform organization-wide actions section:
- Connect to Data Source
- View All Hypervisors
- Use Shared Credentials, under Shared Credentials sub-section
- Run Machine Actions section: Connect to Windows Machine.NoteIf you use Linux machines in your environment, grant the Connect to Linux Machine permission as well.
It's best practice to configure the credentials that you use in the environment as Shared. To learn more, see Configuring Shared Credentials.
Local Policy requirements (pre 9.0)
For versions lower than 9.0, the monitor AD account defined in the monitor requires the Allow Log on Locally user permission on the monitor machine (the service account defined in the Monitor Settings > Domain Identity tab).
Verify the following in Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment:
- The AD account has the Allow log on locally permission.
- The AD account isn't part of the Deny log on locally permission.
Administrative privileges
The ControlUp Monitor can install the ControlUp AgentAgent on machines. For example, machines that are booted up agentless. In Monitor Settings > Domain Identity, we state the following:
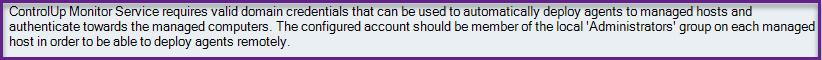
For versions lower than 9.0, it's best practice, but not mandatory, to configure the AD with admin privileges on the endpoint. If you have the ControlUp Agent baked in the golden image or installed on a machine that isn't going to boot without the agent, the AD account used in the monitor can be a non-admin user.