The first login to ControlUp's On-Premises Insights website is done with user Admin and the password configured for the root user. You can keep using the Insights user but you can also use LDAP authentication.
To define LDAP authentication, first access the configuration page:
Go to Admin > Settings > LDAP Configuration > Add LDAP Strategy
LDAP Strategy Name - define the configuration name
LDAP connection settings
Host : Active Directory Domain Controller computer name:
Your IOP server must be able to resolve this host (check via nslookup)
Ports : 389 for non SSL, 636 with SSL. Port 3268 is also required for the Global Catalog service.
SSL enabled: You must also have SSL enabled on your LDAP server.
Connection order : 1
The order in which IOP queries this LDAP server (among enabled servers).
Bind DN If you want a specific user to run the queries, this is the distinguished name used to bind to the LDAP server. In most cases this field should be left blank.
Any user can be used to bind (service account is preferred, password does not change).
For example: CN=IOP LDAP Account,OU=ServiceAccounts,OU=Accounts,DC=controlUp,DC=demo
If you are not sure how to get these details, go to Active Directory Users and Computers and right click the user and choose Properties. Go to attribute editor and look for distinguishedName. Make sure to enable advanced features under the View menu.

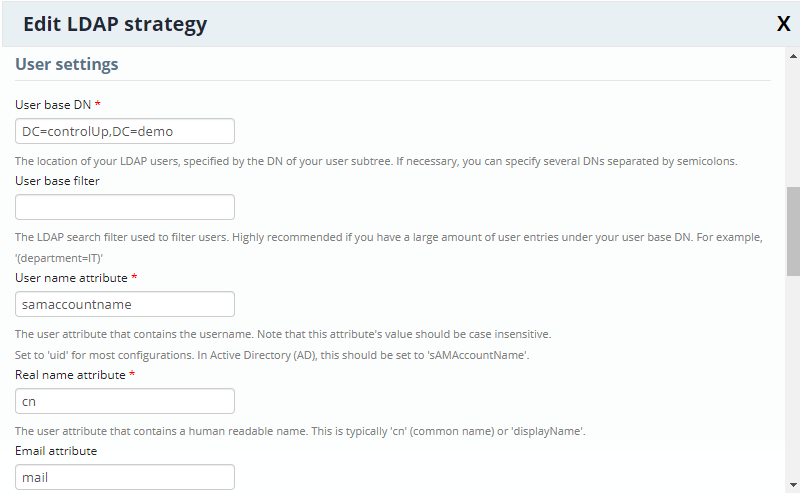
User settings
User base DN
Apply either User settings or Group settings. You can use both.
The location of your LDAP users, specified by the DN of your user subtree. You can specify several DNs separated by semicolons.
For example: DC=controlup,DC=demo
User base filter
Used to filter users. Highly recommended if you have a large amount of user entries under your user base DN. For example: '(department=IT)'
User name attribute
The user attribute that contains the username, usually the sAMAccountName, Note that this attribute's value should be case insensitive.
Real name attribute
The user attribute that contains a human readable name. This is typically 'cn' (common name) or 'displayName'.
Email attribute
The user attribute that contains the user's email address. This is typically 'mail'.
Group mapping attribute
The user attribute that group entries use to define their members. If your LDAP groups use distinguished names for membership, you can leave this field blank.
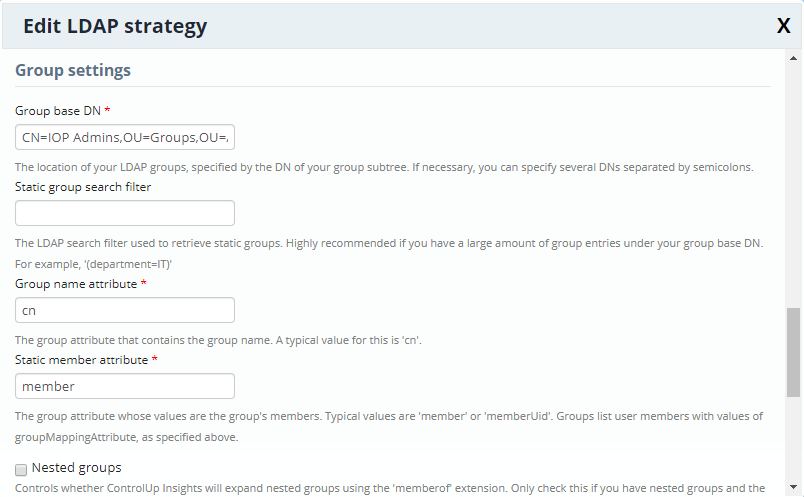
Group settings
Group base DN
Apply either User settings or Group settings. You can use both.
The location of your LDAP groups, specified by the DN of your group subtree. You can specify several DNs separated by semicolons.
This describes the group of users authorized to use insights. For example: CN=IOP Admins,OU=Groups,OU=Accounts,DC=controlUp,DC=demo
Static group search filter
The LDAP search filter used to retrieve static groups. Highly recommended if you have a large amount of group entries under your group base DN. For example, '(department=IT)'
Group name attribute
The group attribute that contains the group name. A typical value for this is 'cn' or 'member'.
Static member attribute
The group attribute whose values are the group's members. Typical values are 'member' or 'memberUid'. Groups list user members with values of groupMappingAttribute.
Nested groups
Controls whether IOP expands nested groups using the 'memberof' extension. Only check this if you have nested groups and the 'memberof' extension on your LDAP server.
Dynamic group settings
Dynamic member attribute
The dynamic group attribute that contains the LDAP URL used to find members. This setting is required to configure dynamic groups. A typical value is 'memberURL'.
Dynamic group search filter
The LDAP search filter used to retrieve dynamic groups (optional). For example, '(objectclass=groupOfURLs)'
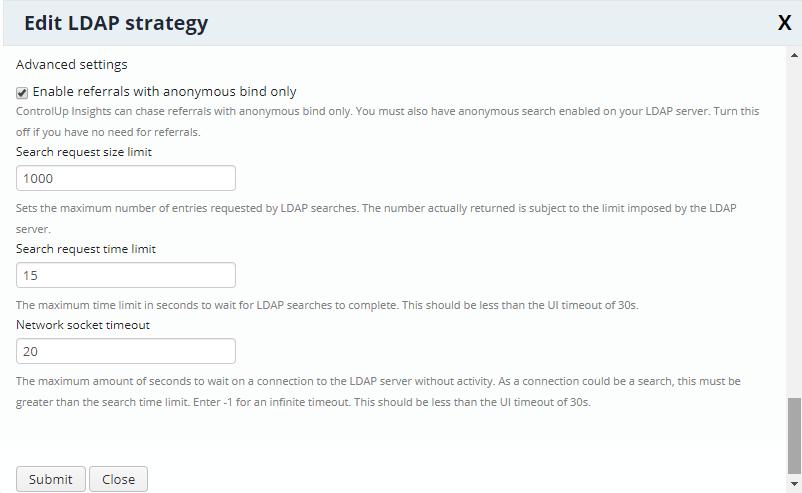
Advanced settings
Checkbox: Enable referrals with anonymous bind only Most of our customers do not enable this option. IOP can use referrals with anonymous bind only but you must also have anonymous search enabled on your LDAP server. Turn this off if you have no need for referrals.
Search request size limit
Sets the maximum number of entries requested by LDAP searches. The number actually returned is subject to the limit imposed by the LDAP server.
Search request time limit
The maximum time limit in seconds to wait for LDAP searches to complete. This should be less than the UI timeout of 30s.
Network socket timeout
The maximum amount of seconds to wait on a connection to the LDAP server without activity. As a connection could be a search, this must be greater than the search time limit. Enter -1 for an infinite timeout.