You can use ControlUp for Desktops to remotely access a device's shell and run commands.
Permissions
- To open a remote shell session on a device, you need the permission Allow Remote Shell.
- To not record the commands you enter into a remote shell, you need the permission Do Not Audit Remote Shell Commands. If you do not have this permission, every command you enter is recorded in the System Events log.
You can set the scope of a permission so that it applies only to certain devices. For example, you can give a user permission to perform an action (such as remote control) only on devices used by the Finance department. Learn more.
Start a remote shell session
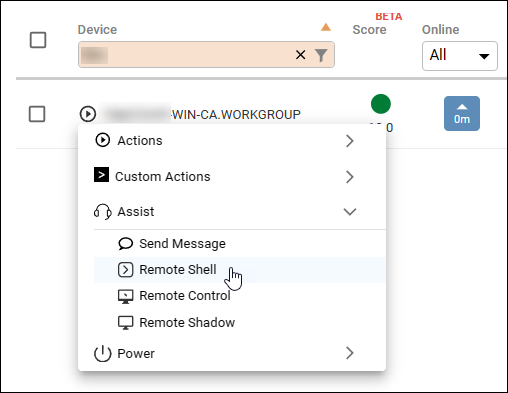
To start a remote shell session on a device:
-
Open the Actions menu for a device and select Assist > Remote Shell.
-
Select a user session for the remote shell or select System or Root to initiate a local system shell.
If you select SYSTEM for a Windows remote shell, you access the local system as NT Authority/SYSTEM which gives you local admin permissions.
- Click Start Remote Shell. The remote shell session opens. The end user of the device is not notified that a remote shell session has been activated.
Remote Shell connection flow
A Remote Shell session is established with the following steps.
- A user requests to start a Remote Shell session on a device from ControlUp. Read above for details on this step.
- A Remote Shell window opens in the ControlUp user's browser and connects to your ControlUp tenant over a websocket.
- Your ControlUp tenant sends an action to the device via the operations websocket (this websocket is initiaited by the device to the tenant).
- The Agent launches a shell executable (hidden from the device user), and a new websocket connection to the tenant. The Agent redirects stdin, stdout, and stderr from the shell process through this new websocket connection.
- The websocket connections opened in steps 2 (from the Remote Shell browser window to the tenant) and 4 (from the Agent to the tenant) are joined through the tenant to connect the Remote Shell browser window to the Agent.
Note that all communications are outbound from the device to the tenant.
Auditing
The System Events log stores the following details about remote shell sessions:
- When the session started and ended.
- Who initiated the session.
- The device that the remote shell session was opened on.
- Every command that was entered in the remote shell. Note that commands are not recorded if the user who initiated the shell session has the permission Do Not Audit Remote Shell Commands.