ControlUp identifies the employee using a device using the following rules:
Device domain account: If the account used to sign into the device is a domain account and the domain is on the approved list, then it identifies the employee.
Application accounts: If the first rule fails to identify the employee, then ControlUp checks the accounts used to sign into applications such as Microsoft Teams and Microsoft 365.
An application account identifies the employee only if the account’s domain is on the approved list. This helps prevent identifying users using non-corporate accounts.
If multiple approved application accounts are found, the one matching the primary domain takes priority. If none of the accounts are in the primary domain, then the most common account is used.
Approved domains
By default, employees in any domain can be identified. You can filter who gets identified by creating a list of approved domains. A user is identified only if their account is in one of the approved domains. When you approve at least one domain, all domains not in the list are excluded.
Creating an approved domains list is required if you want to identify employees using their accounts signed into applications on the device.
To create a list of approved domains:
Go to Settings > Experience Score > Privacy.
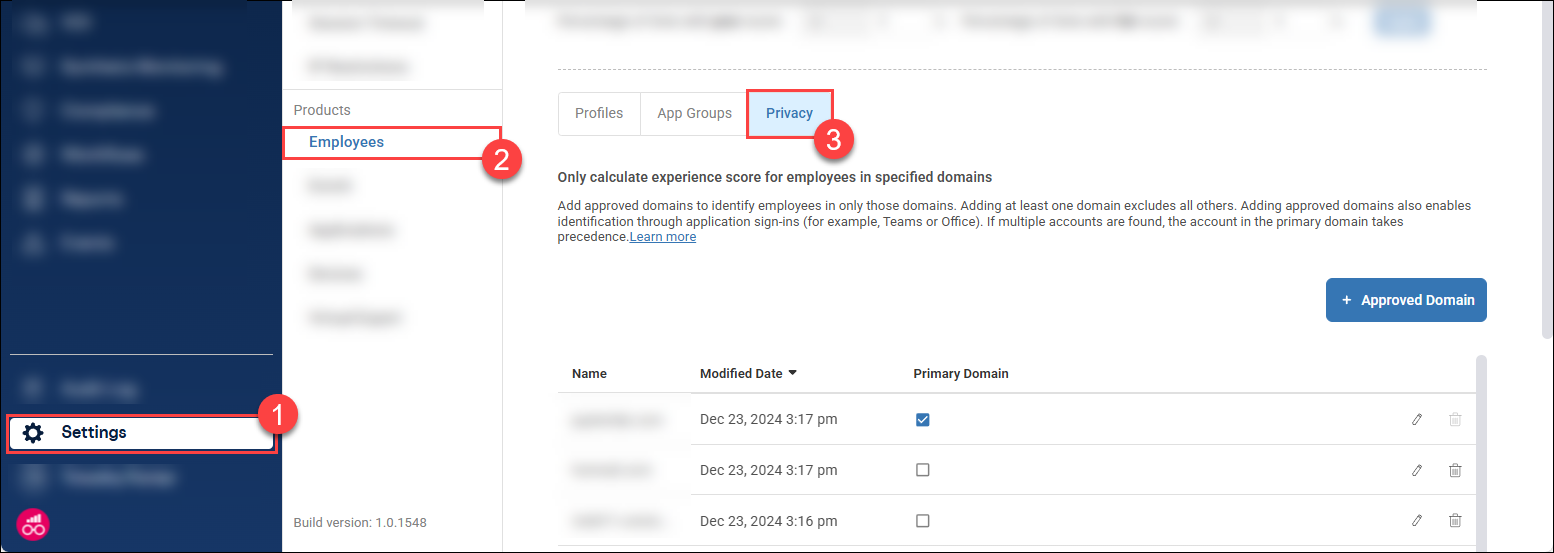
Click +Approve Domain and enter a domain (for example,
controlup.com) and click Submit. Repeat this step to add additional domains.
Primary domain
If you create a list of approved domains, you must set one of the domains to be the Primary Domain. If the account signed in on a device doesn't identify the employee and there are multiple accounts signed in to applications on the device, then the account that matches the primary domain takes priority and is used to identify the employee. If none of the accounts match the primary domain, then the most commonly used account identifies the employee.
Note
Changing the primary domain does not retroactively update previous employee identification or experience scores.
Examples
Identification without an approved domains list
In these scenarios, no domains are in the approved domains list (the default configuration).
Scenario | Result |
|---|---|
| User is identified as |
| User is not identified because the device account is not a domain account, and the account used to sign into the application is not in the approved domains list. |
Identification with an approved domains list
In this scenario, controlup.com is the only approved domain.
Scenario | Result |
|---|---|
| The user is not identified by their device account because |
Identification with a primary domain
In the following scenarios, acme.org and controlup.com are both approved domains. controlup.com is the primary domain.
Scenario | Result |
|---|---|
| The user is identified as |
| The user is identified as |