Use the template tool and the following best practices to maximize the security and manageability of permissions for your ControlUp users. We recommend that you follow these best practices to ensure that users can perform only those actions that are applicable to their roles. You can set permissions and roles in the in the Security Policy Pane of the Real-Time Console.
For more details about the Security Policy Pane, see Security Policy Overview.
To learn how to manage roles, watch our video.
Security Policy Planning Template
For a detailed planning template listing all permissions that you can set, see the Security Policy Planning Sheet. You can use this template as a draft for setting the permissions in the Security Policy Pane. Benefits of using this template to plan your roles and permissions before setting them in the console include:
Fully searchable spreadsheet.
All items are expanded by default.
You can visually see the impact that setting a permission might have on other permissions. For example, if you set Deny on a series of permissions, you can see that the same Deny is inherited by other groups of permissions.
Test your settings ahead of time before implementing them in the console.
To get the most of this template spreadsheet, make a copy to your own location either online or locally, and edit it as follows:
In the Google Sheets menu, select File > Make a copy to save it to a location in your Google Drive. Or you can select File > Download and select a file type to save it locally.
If you want to specify different permissions for different folders in your organization that you don't want inherited from the root folder, duplicate the spreadsheet for each folder: click the spreadsheet name at the bottom and then select Duplicate.
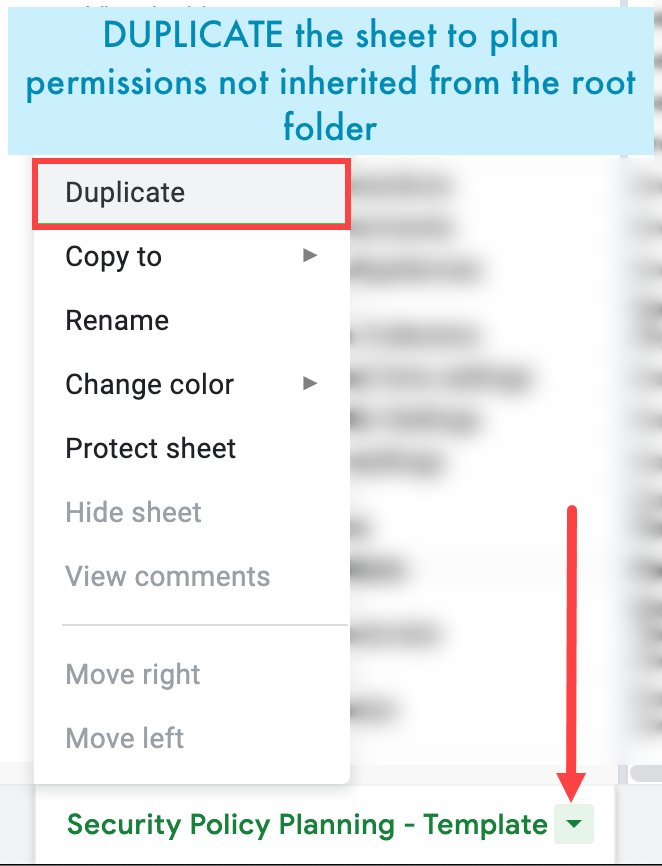
You can now use this spreadsheet as a planning template to set permissions for different roles on your different folders. Follow your selections in this template when working in the Real-Time Console Security Policy Pane.
Best Practices Overview
Best Practice #1 – Set a group of users as organization owners instead of a user
Only specific users called organization owners can set and change permissions for other users. This role is powerful and it is important to know who it is assigned to. By default, the user who creates the organization automatically becomes the organization owner.
It is best practice to configure a dedicated Active Directory group that contains only those users who should be allowed to set ControlUp related permissions. This prevents any single point of failure, for example when the original organization owner can’t be contacted anymore.
See Change Organization Owner to learn how to change the organization owner.
Best Practice #2 – Create Additional User Roles to Better Organize Permissions
Make sure that ControlUp users receive only those permissions that are needed to fulfill a specific task. Managing such permissions can be a complex task, especially in larger organizations.
By default, the ControlUp Real-Time Console automatically creates a set of user roles which are:
Local Admins
Organization Members
Automation Admins
Helpdesk
ControlUp Admins
It is a best practice to create additional roles for different teams or individuals.
See Organization Ownership and User Roles for information about adding roles to the ControlUp Security Pane.
Best Practice #3 - Configure Organization Members to Access the ControlUp Platform to "Not Set"
The Organization Members role is analogous to the Everyone group in Windows. By default, all organization members are allowed to access the ControlUp platform.
It is a best practice to set all permissions for the Organization Members role to Not Set.
See Granting permissions to learn how to set the permission Not Set to a specific role.
Best Practice #4 - Create a Dedicated User Role for Monitors
It is best practice to create a dedicated role for the monitor service. Set permissions for the following actions to Allow: Connect to Windows Machine.
See Configuring Security Policy for Subfolders to learn more about how to set permissions for a specific subfolder.
Best Practice #5 – Restrict Manage Script Actions Permission
Users with the Manage Script Actions permission can write and import their own scripts. This may cause harm to any machine that is reachable from the ControlUp Real-Time Console.
It is a best practice to allow only ControlUp Admins to manage script actions.
See Configuring Security Policy for Subfolders to learn how to set permissions for a specific subfolder.
Best Practice #6 – Create a "View Only" Role
Grant read-only permissions to users who should only view objects in the Real-Time Console without the ability to modify them.
See Security Policy - View Only Role to learn how to configure a View Only security role.