At ControlUp we care about your security and are committed to the protection of your company’s infrastructure and data. ControlUp for Desktops has a robust security architecture comprising multiple security measures, designed to minimize the exposure of your company’s networks and systems to invasive or malicious activity.
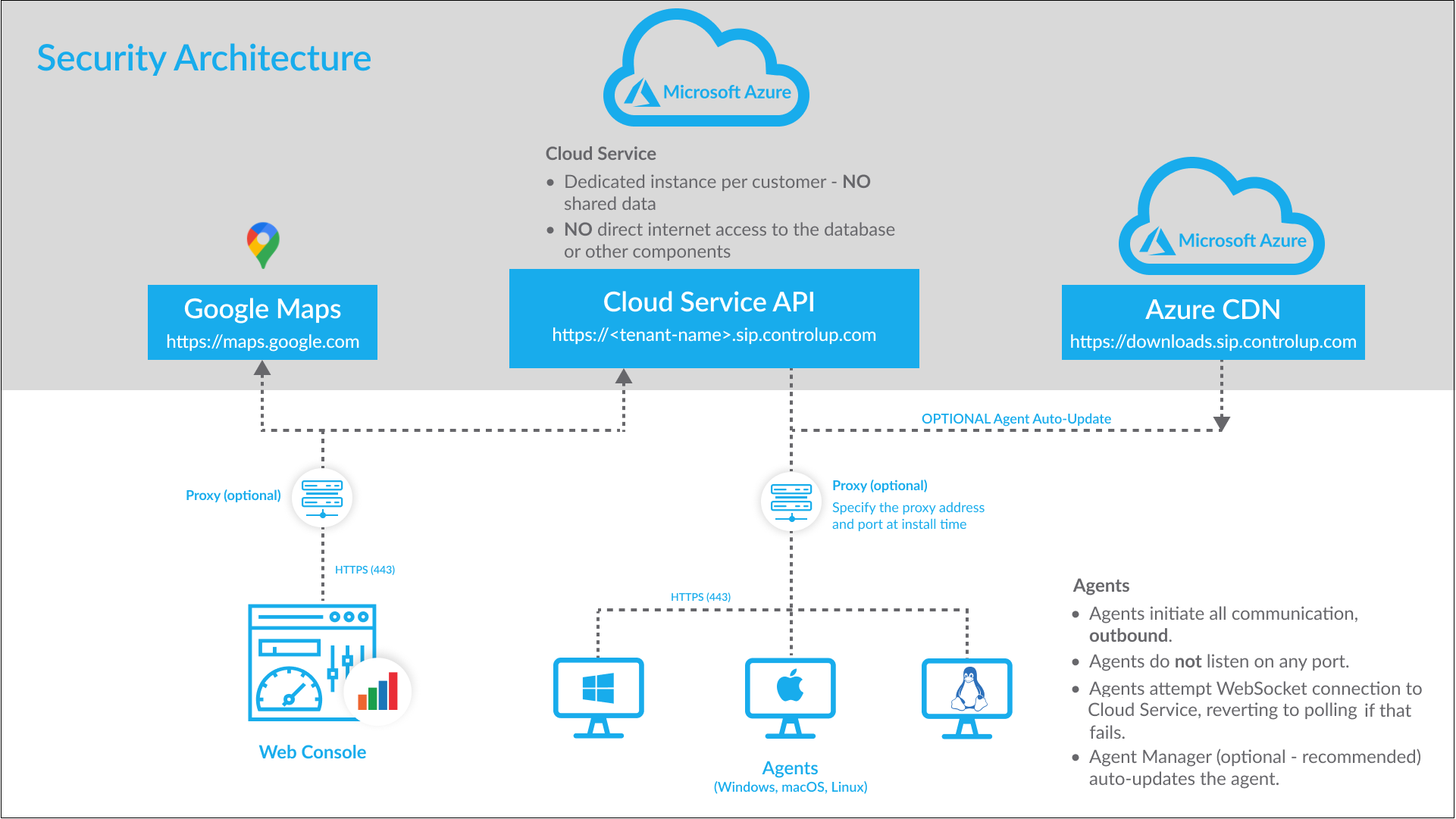
Secure Cloud Service
ControlUp for Desktops uses the Microsoft Azure Cloud Service.
- There is a dedicated instance per customer – absolutely zero data is shared.
For additional information about the storage of your cloud data, please contact your ControlUp representative.
Secure Data Transmission
Data transmission for ControlUp for Desktops:
- All data travels over port 443 on HTTPS using TLS 1.2 or higher.
Secure Communication between the Agent and the Backend in the Cloud
Communication between the ControlUp for Desktops Agent and the ControlUp backend in the cloud is secured:
- All communication is initiated outbound by the agent. The agent does not listen on any port.
- The agent attempts to establish a WebSocket to the Cloud Service. If this fails, it reverts to polling.
- The (optional) Agent Manager auto-updates the agent from downloads.sip.controlup.com, which uses the Azure CDN.
Data Collection and Retention
- Data is retained for each device for a minimum of 28 days.
- Core performance metrics are gathered every 60 seconds.
- If the connection between an endpoint and ControlUp is temporarily interrupted, data is cached locally in the file system while the endpoint is offline. The data is uploaded as soon as the connection is restored. The only limit to the amount of data which can be stored locally is the file system, but typically the stored data amounts to only a few MB a week.
Role-based access control
ControlUp for Desktops features are secured using role-based access control.
Security Best Practices
Adherence to recommended security best practices minimize the exposure of your company’s networks and systems to invasive or malicious activity.
We recommend the following to optimize the security of your company’s networks and systems:
Agent Updates
- For OS platforms that support it, we recommend distributing the Agent Manager which automatically updates the Agent with the versions that you set in your version control settings. Learn more about Agent version control.
- If you opt not to use the Agent Manager to automatically update the Agents, and instead manually update the Agent on each machine, update agents at least every 6 months to take advantage of fixes and new functionality.