The User Risk Analytics feature helps you improve your organization's security by identifying employees performing risky logins to SaaS applications (including VPNs).
ControlUp determines an employee's level of risk based on the following factors:
- Devices - Unmanaged devices are risky because their security status is unknown. The risk from a managed device is calculated based on compliance with your Templates.
- Authentication methods - Logins performed with a username/password have a higher risk than logins with SSO through your identity provider.
- Application security - ControlUp determines SaaS application security by analyzing the application's SSL certificate. Weak ciphers or untrustworthy publishers increase an application's risk.
After identifying risky logins based on the factors above, you can implement a solution to improve security. Potential solutions could be:
- Informing employees not to access corporate resources from personal devices.
- Reviewing unapproved apps (known as "shadow IT") to see if they are safe. If they are safe to use, you can add them to your Identity Provider to improve security.
- Patching or reconfiguring managed devices to improve endpoint security.
How to set up this feature
To access the settings page described in this section, go to Compliance > Configuration > User Risk Analytics.
Step 1 - Integrate with your identity provider
ControlUp uses sign-in logs from your identity provider (Entra ID or Okta) to identify logins performed through your identity provider.
- Depending on which identity provider you use, perform the steps in one of the following articles to set up the integration. The Purpose for the connections must be set to ControlUp for Compliance.
- In the ControlUp for Compliance settings page, go to User Risk Analytics.
- Enable the Identity provider connections settings and select the integrations you created.
- In the Login Event Logs Retention Period field, set how long ControlUp stores login event data. The retention period applies to data from your identity provider and the browser extension.
- In the Operating System assignment field, select the operations systems from which to collect identity provider sign-in logs. ControlUp shows identity provider login data only if the login was performed from devices with the selected operating systems.
Step 2 - Exclude your web gateways
Under the Excluded gateway IP addresses field, enter the IP addresses of your web gateways (for example, those used in your company's offices).
In some situations, a device is identified by its IP address (if the browser extension isn't installed or if the identity provider login isn't performed through a browser). Excluding your web gateways prevents devices behind the gateway from being misidentified.
An unknown device behind a web gateway can't be identified and appears as an "unknown device" with a yellow icon to let you know it is behind a gateway. If you would rather hide data from these unknown devices, click Don't collect data for unknown devices behind a gateway.
Step 3 - Deploy the browser extension
ControlUp uses login request data from the browser extension to identify the device used to login through your identity provider, and to record logins that aren't performed through your identity provider (with a username and password). You can deploy the browser extension to devices with the ControlUp for Compliance Agent installed. The browser extension supports Chromium-based browsers such as Chrome, Edge, and Opera.
To deploy the browser extension:
- Enable the Browser extension deployment setting.
- Select which devices to install the browser extension on by targeting device groups or device tags.
The browser extension is automatically installed on all devices that have the ControlUp for Compliance Agent installed and match your device targets.
Step 4 - Add your corporate domains
In the Approved domains field, add the domains for which you want to collect login information. The browser extension collects login information only for logins performed with a domain on the list. For example, if @controlup.com is the only domain on the list, ControlUp will not collect data when an employee signs into an application with their personal @gmail.com account.
See login details for all users
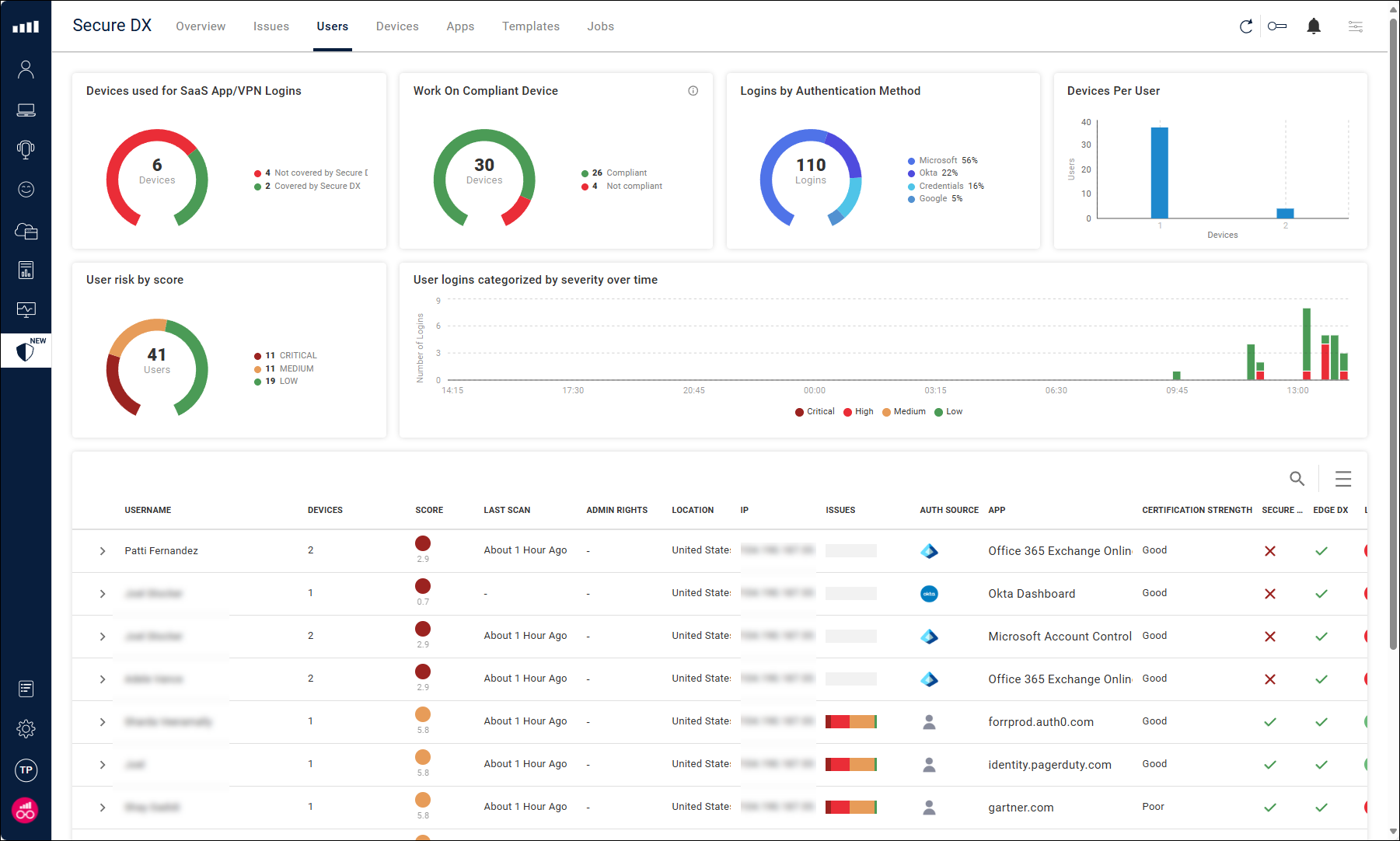
The Users page shows a summary of SaaS app logins across all users, with the following widgets for login data:
- Devices Used for SaaS App/VPN Logins. Shows you how many devices are used for SaaS app logins, broken down by whether the device is covered by ControlUp for Compliance.
- Logins by Authentication Method. The total number of app logins, broken down by the authentication method.
- User logins categorized by severity over time. Shows the number of SaaS app logins over time with the level of risk for each login.
This page also contains a list of all users, including details about their last app login (the app, authentication method, app certificates, and risk level), and whether the ControlUp for Compliance/Desktops Agent is installed on their devices. Click the arrow next to a user's name to see a list of devices they have used.
See login details for a specific user
Click on a user from the table to drill down into the details page for that user. The details page shows you information about the user's security score, devices they are using, SaaS app logins, and issues detected on the user's devices.
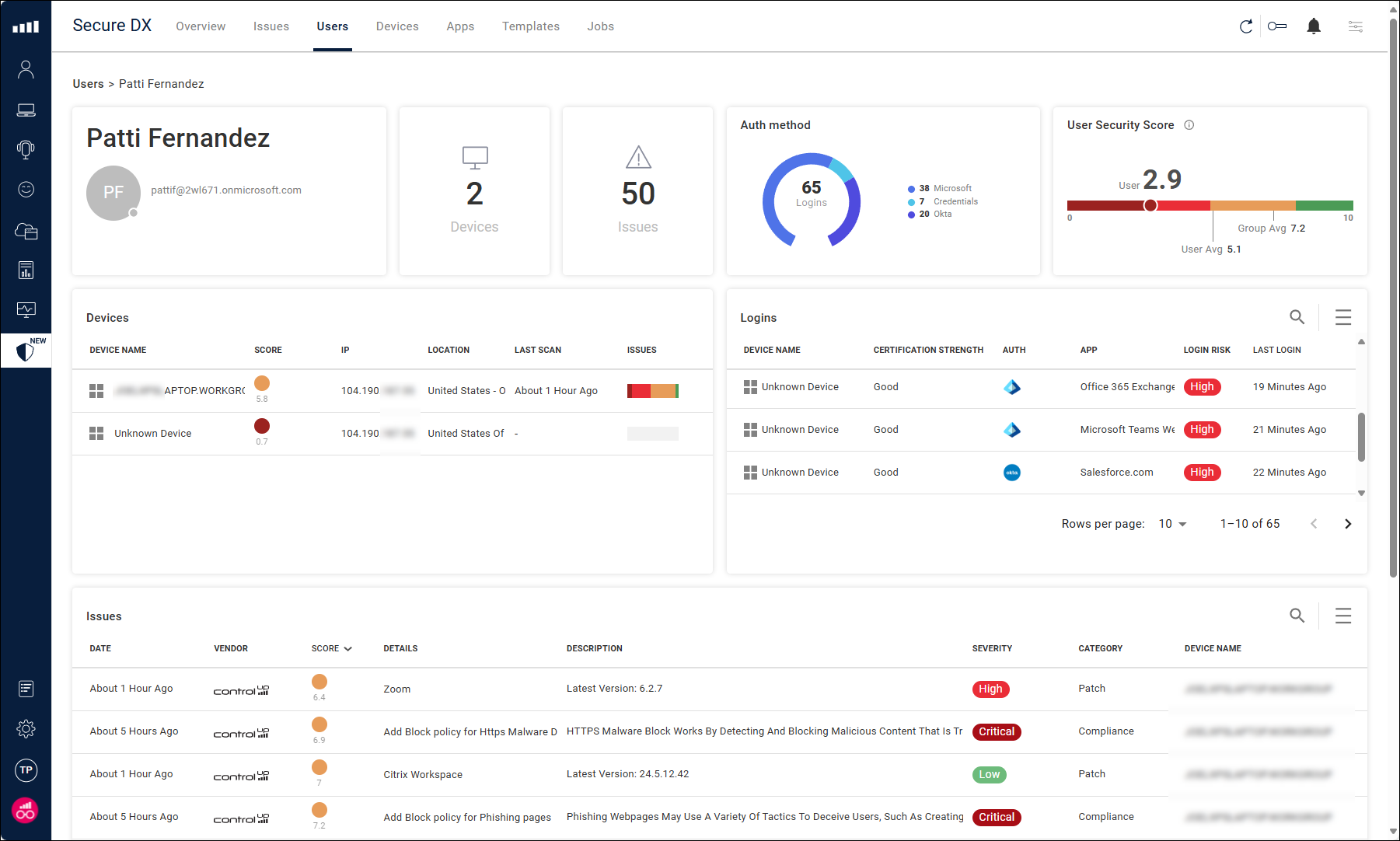
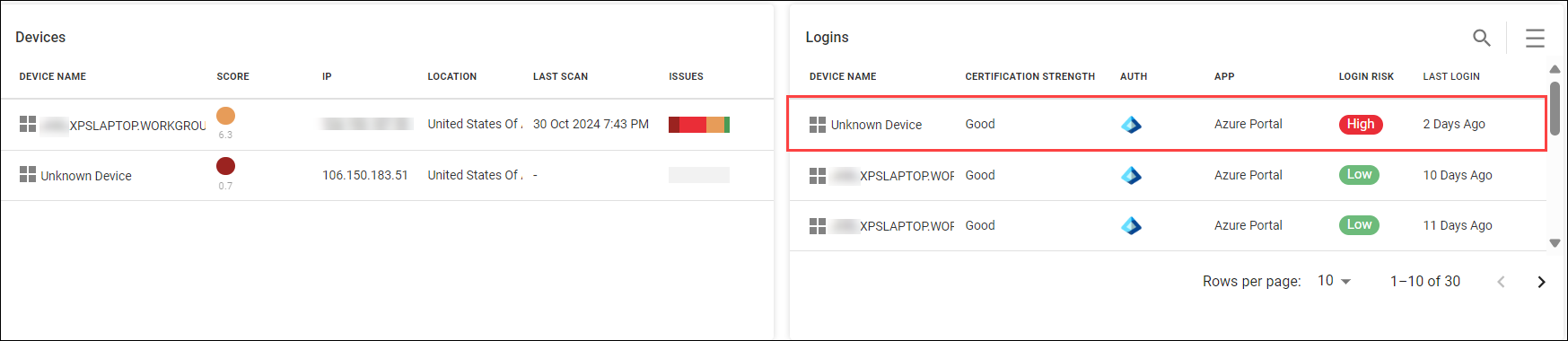
The Devices widget shows all devices used by the employee. The Logins widget shows all SaaS application login events and their associated risk.
For example, the image below shows a login with a high risk. In this case, the application (Azure portal) has strong certificates and Entra ID was used for authentication, but the login was performed from an unknown device which causes the login event to have a high risk.
Risky SaaS app logins are reported as security issues and are listed in the Issues table (as well as on the main Issues page). These issues are reported with the issue category Identity.
See a summary of SaaS apps used in your environment
On the Apps tab, select SaaS to view a list of all SaaS apps used in your environment. This page also includes widgets to show the total number of SaaS apps broken down by login method and security certification strength.
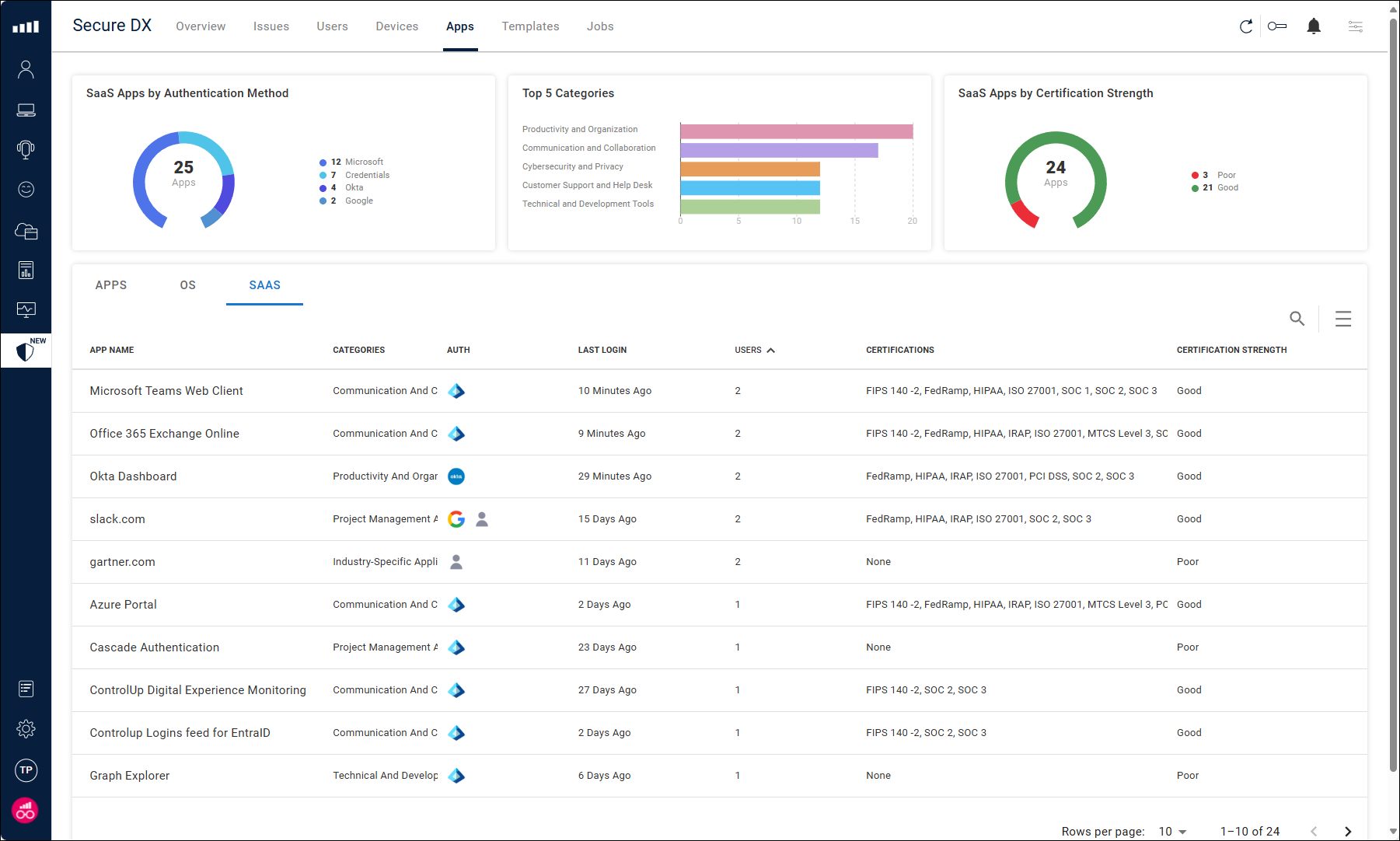
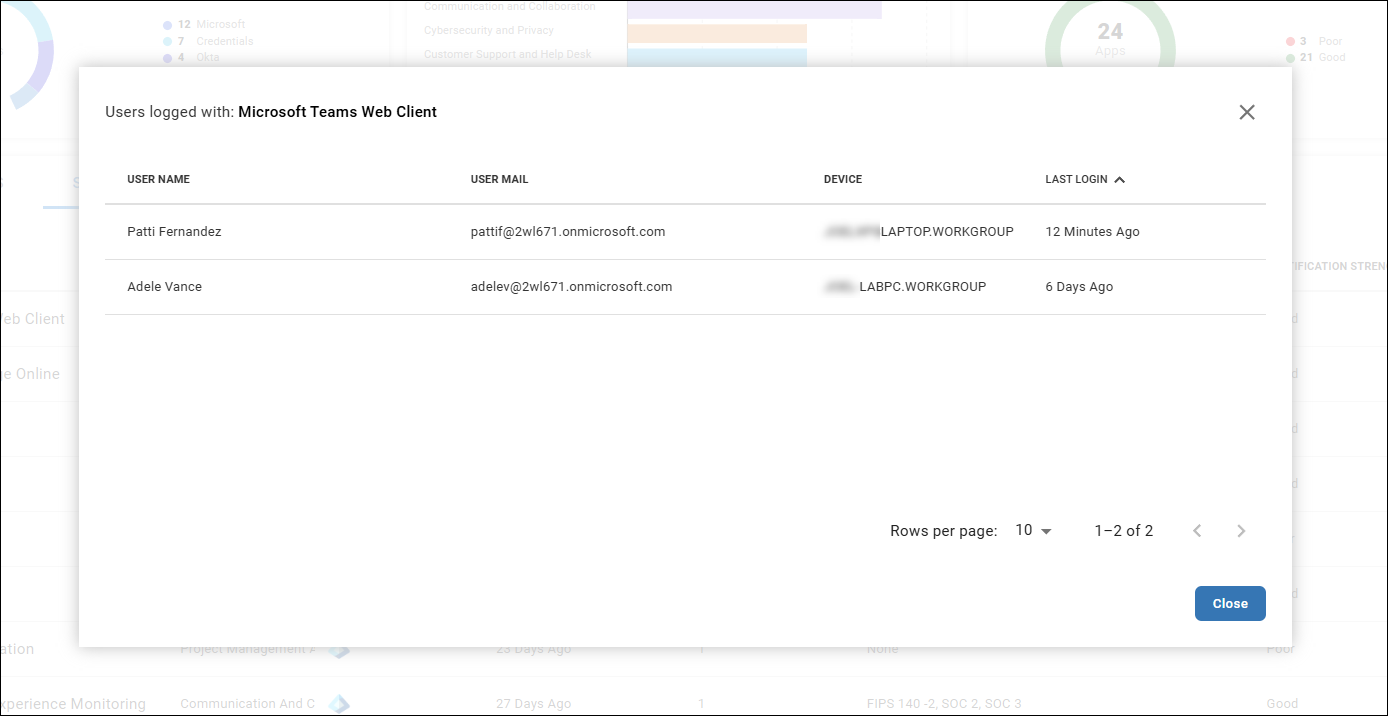
Click on the number of users in the Users column to see who used the application, and when.
Troubleshooting
Why is a device appearing as "Unknown Device"?
"Unknown device" means that there is a sign-in event in your identity provider logs but the login can't be traced to a device because both of the following points are true:
- The device used doesn't have the browser extension installed or the login wasn't performed through a supported browser.
- The IP address from the identity provider log doesn't correspond to one of your devices managed by ControlUp for Desktops.
If you don't find this login data from unknown devices valuable and you want to reduce the number of logins reported from unknown devices, you can:
- Select Don't collect data from unknown devices behind a gateway in your ControlUp for Compliance gateway settings.
- Limit the operating systems for identity provider log collection. For example, ControlUp for Compliance might be reporting sign-in events from mobile devices that can't be identified.
Why don't I see a login event?
A login event appears in ControlUp if at least one of the following conditions must be met:
- There is a sign-in event in your identity provider logs from one of the selected operating systems. Because login data is pulled from your identity provider, there might be a delay between when the login event occurs and when the identity provider data appears in the ControlUp UI.
- A device with the browser extension installed performed a login using one of the approved domains.